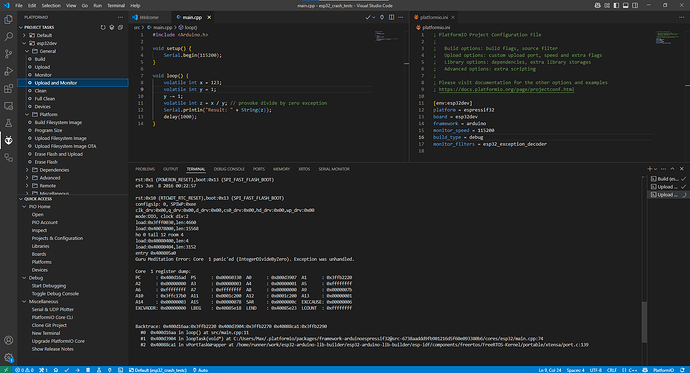
I am using Platformio Core 6.1.11 on a Mac. Very rarely, the esp32 code I am debugging crashes and I would like to use the exception decoder to understand the reasons of the crash.
I added “monitor_filters = esp32_exception_decoder” to the platformio.ini file but I do not get any decoding analysis of the crash. I cannot work out what is missing or I am doing wrong.
I did use this feature before in another project and it did work…
Can anybody please give me some help?
Here is my platformio.ini file:
[env:esp32doit-devkit-v1]
platform = espressif32
board = esp32doit-devkit-v1
framework = arduino
monitor_speed = 115200
lib_deps =
fastled/FastLED
ArduinoJson
https://github.com/Links2004/arduinoWebSockets.git
paulstoffregen/Time@^1.6.1
arduino-libraries/NTPClient@^3.1.0
https://github.com/me-no-dev/ESPAsyncWebServer.git
ayushsharma82/AsyncElegantOTA@^2.2.7
robtillaart/PCF8575@^0.1.6
robtillaart/SHT31@^0.3.6
robtillaart/TCA9548@^0.1.2
https://github.com/Atlas-Scientific/Ezo_I2c_lib.git
build_flags =
-D CORE_DEBUG_LEVEL=0
board_build.partitions = partitions.csv
monitor_filters = esp32_exception_decoder
And this is the output I get when the crash occurs:
2024-01-03 12:18:00 Guru Meditation Error: Core 1 panic'ed (Cache disabled but cached memory region accessed).
2024-01-03 12:18:00
2024-01-03 12:18:00 Core 1 register dump:
2024-01-03 12:18:00 PC : 0x400ed148 PS : 0x00060035 A0 : 0x800814d2 A1 : 0x3ffbf55c
2024-01-03 12:18:00 A2 : 0x3ffc4210 A3 : 0x00000000 A4 : 0x00060023 A5 : 0x80000000
2024-01-03 12:18:00 A6 : 0x007bf608 A7 : 0x003fffff A8 : 0x80081479 A9 : 0x00000000
2024-01-03 12:18:00 A10 : 0x00000000 A11 : 0x00000000 A12 : 0x0000001a A13 : 0x80000000
2024-01-03 12:18:00 A14 : 0x00000002 A15 : 0x3ffc4148 SAR : 0x00000020 EXCCAUSE: 0x00000007
2024-01-03 12:18:00 EXCVADDR: 0x00000000 LBEG : 0x00000000 LEND : 0x00000000 LCOUNT : 0x00000000
2024-01-03 12:18:00
2024-01-03 12:18:00
2024-01-03 12:18:00 Backtrace: 0x400ed145:0x3ffbf55c |<-CORRUPTED
2024-01-03 12:18:00
2024-01-03 12:18:00
2024-01-03 12:18:00
2024-01-03 12:18:00
2024-01-03 12:18:00 ELF file SHA256: 553661430b3ebb5d
2024-01-03 12:18:00
2024-01-03 12:18:00 Rebooting...
2024-01-03 12:18:00 ets Jul 29 2019 12:21:46
2024-01-03 12:18:00
2024-01-03 12:18:00 rst:0x3 (SW_RESET),boot:0x13 (SPI_FAST_FLASH_BOOT)
2024-01-03 12:18:00 configsip: 0, SPIWP:0xee
2024-01-03 12:18:00 clk_drv:0x00,q_drv:0x00,d_drv:0x00,cs0_drv:0x00,hd_drv:0x00,wp_drv:0x00
2024-01-03 12:18:00 mode:DIO, clock div:2
2024-01-03 12:18:00 load:0x3fff0030,len:1184
2024-01-03 12:18:00 load:0x40078000,len:13104
2024-01-03 12:18:00 load:0x40080400,len:3036
2024-01-03 12:18:00 entry 0x400805e4
2024-01-03 12:18:01 [WDT] Panic (hardware watchdog) reset
Partitions do include a “coredump” area:
#Name, Type, SubType, Offset, Size
nvs, data, nvs, 0x9000, 16K
phy_init, data, phy, 0xD000, 4K
otadata, data, ota, 0xE000, 8K
app0, app, ota_0, 0x10000, 1920K
app1, app, ota_1, 0x1F0000, 1920K
config, data, spiffs, 0x3D0000, 32K
webif, data, spiffs, 0x3D8000, 96K
coredump, data, coredump, 0x3F0000, 64K