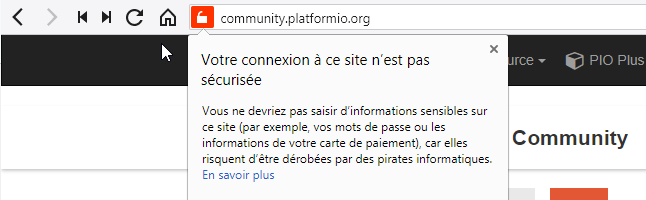
It seems that The platformio cummunity forum is not secured with https (this is what Vivaldi navigator shows)
My navigator: Vivaldi
My OS: Windows 8.1
It seems that The platformio cummunity forum is not secured with https (this is what Vivaldi navigator shows)

My navigator: Vivaldi
My OS: Windows 8.1
It gave me this
Certificate #1: RSA 2048 bits (SHA256withRSA)
Server Key and Certificate #1
Subject community.platformio.org
Fingerprint SHA256: 1885f55bef32ff27b6afd3332ce791fbad84482a8dadf07827bb9f603953ffef
Pin SHA256: ACJAXgQ9vbTsTEAqK6oAZF/etYIeqh2eud1cgeeWyXg=
Common names community.platformio.org
Alternative names community.platformio.org
Serial Number 0448f4b6455cdec27818cb70d5149af011d5
Valid from Sat, 04 Aug 2018 11:36:41 UTC
Valid until Fri, 02 Nov 2018 11:36:41 UTC (expires in 1 month and 29 days)
Key RSA 2048 bits (e 65537)
Weak key (Debian) No
Issuer Let's Encrypt Authority X3
AIA: http://cert.int-x3.letsencrypt.org/
Signature algorithm SHA256withRSA
Extended Validation No
Certificate Transparency Yes (certificate)
OCSP Must Staple No
Revocation information OCSP
OCSP: http://ocsp.int-x3.letsencrypt.org
Revocation status Good (not revoked)
DNS CAA No (more info)
Trusted Yes
Mozilla Apple Android Java Windows
Additional Certificates (if supplied)
Certificates provided 2 (2740 bytes)
Chain issues None
#2
Subject Let's Encrypt Authority X3
Fingerprint SHA256: 25847d668eb4f04fdd40b12b6b0740c567da7d024308eb6c2c96fe41d9de218d
Pin SHA256: YLh1dUR9y6Kja30RrAn7JKnbQG/uEtLMkBgFF2Fuihg=
Valid until Wed, 17 Mar 2021 16:40:46 UTC (expires in 2 years and 6 months)
Key RSA 2048 bits (e 65537)
Issuer DST Root CA X3
Signature algorithm SHA256withRSA
Hide Certification Paths Certification Paths
MozillaAppleAndroidJavaWindows
Path #1: Trusted
1 Sent by server community.platformio.org
Fingerprint SHA256: 1885f55bef32ff27b6afd3332ce791fbad84482a8dadf07827bb9f603953ffef
Pin SHA256: ACJAXgQ9vbTsTEAqK6oAZF/etYIeqh2eud1cgeeWyXg=
RSA 2048 bits (e 65537) / SHA256withRSA
2 Sent by server Let's Encrypt Authority X3
Fingerprint SHA256: 25847d668eb4f04fdd40b12b6b0740c567da7d024308eb6c2c96fe41d9de218d
Pin SHA256: YLh1dUR9y6Kja30RrAn7JKnbQG/uEtLMkBgFF2Fuihg=
RSA 2048 bits (e 65537) / SHA256withRSA
3 In trust store DST Root CA X3 Self-signed
Fingerprint SHA256: 0687260331a72403d909f105e69bcf0d32e1bd2493ffc6d9206d11bcd6770739
Pin SHA256: Vjs8r4z+80wjNcr1YKepWQboSIRi63WsWXhIMN+eWys=
RSA 2048 bits (e 65537) / SHA1withRSA
Weak or insecure signature, but no impact on root certificate
Certificate #2: RSA 2048 bits (SHA256withRSA) No SNI Hide Server Certificate
Server Key and Certificate #1
Subject pioplus.com
Fingerprint SHA256: 09e858adc5f861266e94b88929d43e3547a8f285994d3ce580c9748f9250c437
Pin SHA256: PwDzNEDnBl4O809ASONMnoz1rN1y38+/VlO7dMTEk8M=
Common names pioplus.com
Alternative names pioplus.com MISMATCH
Serial Number 0494448a437bfcbcbcc2463da077f5e62679
Valid from Sat, 04 Aug 2018 11:37:00 UTC
Valid until Fri, 02 Nov 2018 11:37:00 UTC (expires in 1 month and 29 days)
Key RSA 2048 bits (e 65537)
Weak key (Debian) No
Issuer Let's Encrypt Authority X3
AIA: http://cert.int-x3.letsencrypt.org/
Signature algorithm SHA256withRSA
Extended Validation No
Certificate Transparency Yes (certificate)
OCSP Must Staple No
Revocation information OCSP
OCSP: http://ocsp.int-x3.letsencrypt.org
Revocation status Good (not revoked)
Trusted No NOT TRUSTED
Mozilla Apple Android Java Windows
Additional Certificates (if supplied)
Certificates provided 2 (2713 bytes)
Chain issues None
#2
Subject Let's Encrypt Authority X3
Fingerprint SHA256: 25847d668eb4f04fdd40b12b6b0740c567da7d024308eb6c2c96fe41d9de218d
Pin SHA256: YLh1dUR9y6Kja30RrAn7JKnbQG/uEtLMkBgFF2Fuihg=
Valid until Wed, 17 Mar 2021 16:40:46 UTC (expires in 2 years and 6 months)
Key RSA 2048 bits (e 65537)
Issuer DST Root CA X3
Signature algorithm SHA256withRSA
Show Certification Paths Certification Paths
Click here to expand
Configuration
Protocols
TLS 1.3 No
TLS 1.2 Yes
TLS 1.1 Yes
TLS 1.0 Yes
SSL 3 No
SSL 2 No
For TLS 1.3 tests, we currently support draft version 28.
Cipher Suites
# TLS 1.2 (server has no preference)
TLS_RSA_WITH_AES_128_CBC_SHA (0x2f) WEAK 128
TLS_RSA_WITH_CAMELLIA_128_CBC_SHA (0x41) WEAK 128
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA (0xc013) ECDH secp256r1 (eq. 3072 bits RSA) FS 128
TLS_RSA_WITH_AES_128_CBC_SHA256 (0x3c) WEAK 128
TLS_RSA_WITH_AES_128_GCM_SHA256 (0x9c) WEAK 128
TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA256 (0xc027) ECDH secp256r1 (eq. 3072 bits RSA) FS 128
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 (0xc02f) ECDH secp256r1 (eq. 3072 bits RSA) FS 128
TLS_RSA_WITH_AES_256_CBC_SHA (0x35) WEAK 256
TLS_RSA_WITH_CAMELLIA_256_CBC_SHA (0x84) WEAK 256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA (0xc014) ECDH secp256r1 (eq. 3072 bits RSA) FS 256
TLS_RSA_WITH_AES_256_CBC_SHA256 (0x3d) WEAK 256
TLS_RSA_WITH_AES_256_GCM_SHA384 (0x9d) WEAK 256
TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 (0xc028) ECDH secp256r1 (eq. 3072 bits RSA) FS 256
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030) ECDH secp256r1 (eq. 3072 bits RSA) FS 256
# TLS 1.1 (server has no preference)
# TLS 1.0 (server has no preference)
# TLS 1.0 No SNI (suites in server-preferred order)
Handshake Simulation
Android 2.3.7 No SNI 2 Incorrect certificate because this client doesn't support SNI
RSA 2048 (SHA256) | TLS 1.0 | TLS_DHE_RSA_WITH_AES_128_CBC_SHA | DH 4096
Android 4.0.4 RSA 2048 (SHA256) TLS 1.0 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
Android 4.1.1 RSA 2048 (SHA256) TLS 1.0 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
Android 4.2.2 RSA 2048 (SHA256) TLS 1.0 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
Android 4.3 RSA 2048 (SHA256) TLS 1.0 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
Android 4.4.2 RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Android 5.0.0 RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
Android 6.0 RSA 2048 (SHA256) TLS 1.2 > http/1.1 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
Android 7.0 RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
Baidu Jan 2015 RSA 2048 (SHA256) TLS 1.0 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
BingPreview Jan 2015 RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Chrome 49 / XP SP3 RSA 2048 (SHA256) TLS 1.2 > http/1.1 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
Chrome 69 / Win 7 R RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
Firefox 31.3.0 ESR / Win 7 RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
Firefox 47 / Win 7 R RSA 2048 (SHA256) TLS 1.2 > http/1.1 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
Firefox 49 / XP SP3 RSA 2048 (SHA256) TLS 1.2 > http/1.1 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
Firefox 62 / Win 7 R RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
Googlebot Feb 2018 RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256 ECDH secp256r1 FS
IE 7 / Vista RSA 2048 (SHA256) TLS 1.0 TLS_RSA_WITH_AES_128_CBC_SHA No FS
IE 8 / XP No FS 1 No SNI 2 Incorrect certificate because this client doesn't support SNI
RSA 2048 (SHA256) | TLS 1.0 | TLS_RSA_WITH_3DES_EDE_CBC_SHA
IE 8-10 / Win 7 R RSA 2048 (SHA256) TLS 1.0 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
IE 11 / Win 7 R RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
IE 11 / Win 8.1 R RSA 2048 (SHA256) TLS 1.2 > http/1.1 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
IE 10 / Win Phone 8.0 RSA 2048 (SHA256) TLS 1.0 TLS_RSA_WITH_AES_128_CBC_SHA No FS
IE 11 / Win Phone 8.1 R RSA 2048 (SHA256) TLS 1.2 > http/1.1 TLS_RSA_WITH_AES_128_CBC_SHA256 No FS
IE 11 / Win Phone 8.1 Update R RSA 2048 (SHA256) TLS 1.2 > http/1.1 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
IE 11 / Win 10 R RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Edge 15 / Win 10 R RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Edge 13 / Win Phone 10 R RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Java 6u45 No SNI 2 Client does not support DH parameters > 1024 bits
RSA 2048 (SHA256) | TLS 1.0 | TLS_DHE_RSA_WITH_AES_128_CBC_SHA | DH 4096
Java 7u25 RSA 2048 (SHA256) TLS 1.0 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA ECDH secp256r1 FS
Java 8u161 RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
OpenSSL 0.9.8y RSA 2048 (SHA256) TLS 1.0 TLS_RSA_WITH_AES_256_CBC_SHA No FS
OpenSSL 1.0.1l R RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
OpenSSL 1.0.2e R RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Safari 5.1.9 / OS X 10.6.8 RSA 2048 (SHA256) TLS 1.0 TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA ECDH secp256r1 FS
Safari 6 / iOS 6.0.1 RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
Safari 6.0.4 / OS X 10.8.4 R RSA 2048 (SHA256) TLS 1.0 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA ECDH secp256r1 FS
Safari 7 / iOS 7.1 R RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
Safari 7 / OS X 10.9 R RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
Safari 8 / iOS 8.4 R RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
Safari 8 / OS X 10.10 R RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_CBC_SHA384 ECDH secp256r1 FS
Safari 9 / iOS 9 R RSA 2048 (SHA256) TLS 1.2 > http/1.1 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Safari 9 / OS X 10.11 R RSA 2048 (SHA256) TLS 1.2 > http/1.1 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Safari 10 / iOS 10 R RSA 2048 (SHA256) TLS 1.2 > http/1.1 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Safari 10 / OS X 10.12 R RSA 2048 (SHA256) TLS 1.2 > http/1.1 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Apple ATS 9 / iOS 9 R RSA 2048 (SHA256) TLS 1.2 > http/1.1 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
Yahoo Slurp Jan 2015 RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
YandexBot Jan 2015 RSA 2048 (SHA256) TLS 1.2 TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 ECDH secp256r1 FS
# Not simulated clients (Protocol mismatch)
IE 6 / XP No FS 1 No SNI 2 Protocol mismatch (not simulated)
(1) Clients that do not support Forward Secrecy (FS) are excluded when determining support for it.
(2) No support for virtual SSL hosting (SNI). Connects to the default site if the server uses SNI.
(3) Only first connection attempt simulated. Browsers sometimes retry with a lower protocol version.
(R) Denotes a reference browser or client, with which we expect better effective security.
(All) We use defaults, but some platforms do not use their best protocols and features (e.g., Java 6 & 7, older IE).
(All) Certificate trust is not checked in handshake simulation, we only perform TLS handshake.
Protocol Details
DROWN No, server keys and hostname not seen elsewhere with SSLv2
(1) For a better understanding of this test, please read this longer explanation
(2) Key usage data kindly provided by the Censys network search engine; original DROWN website here
(3) Censys data is only indicative of possible key and certificate reuse; possibly out-of-date and not complete
Secure Renegotiation Supported
Secure Client-Initiated Renegotiation No
Insecure Client-Initiated Renegotiation No
BEAST attack Not mitigated server-side (more info) TLS 1.0: 0x2f
POODLE (SSLv3) No, SSL 3 not supported (more info)
POODLE (TLS) No (more info)
Downgrade attack prevention Yes, TLS_FALLBACK_SCSV supported (more info)
SSL/TLS compression No
RC4 No
Heartbeat (extension) Yes
Heartbleed (vulnerability) No (more info)
Ticketbleed (vulnerability) No (more info)
OpenSSL CCS vuln. (CVE-2014-0224) No (more info)
OpenSSL Padding Oracle vuln.
(CVE-2016-2107) No (more info)
ROBOT (vulnerability) No (more info)
Forward Secrecy With some browsers (more info)
ALPN No
NPN Yes http/1.1
Session resumption (caching) Yes
Session resumption (tickets) Yes
OCSP stapling No
Strict Transport Security (HSTS) No
HSTS Preloading Not in: Chrome Edge Firefox IE
Public Key Pinning (HPKP) No (more info)
Public Key Pinning Report-Only No
Public Key Pinning (Static) No (more info)
Long handshake intolerance No
TLS extension intolerance No
TLS version intolerance No
Incorrect SNI alerts No
Uses common DH primes No, DHE suites not supported
DH public server param (Ys) reuse No, DHE suites not supported
ECDH public server param reuse No
Supported Named Groups secp256r1
SSL 2 handshake compatibility Yes
HTTP Requests
1 https://community.platformio.org/ (HTTP/1.1 200 OK)
Miscellaneous
Test date Mon, 03 Sep 2018 12:50:12 UTC
Test duration 165.521 seconds
HTTP status code 200
HTTP server signature nginx
Server hostname -